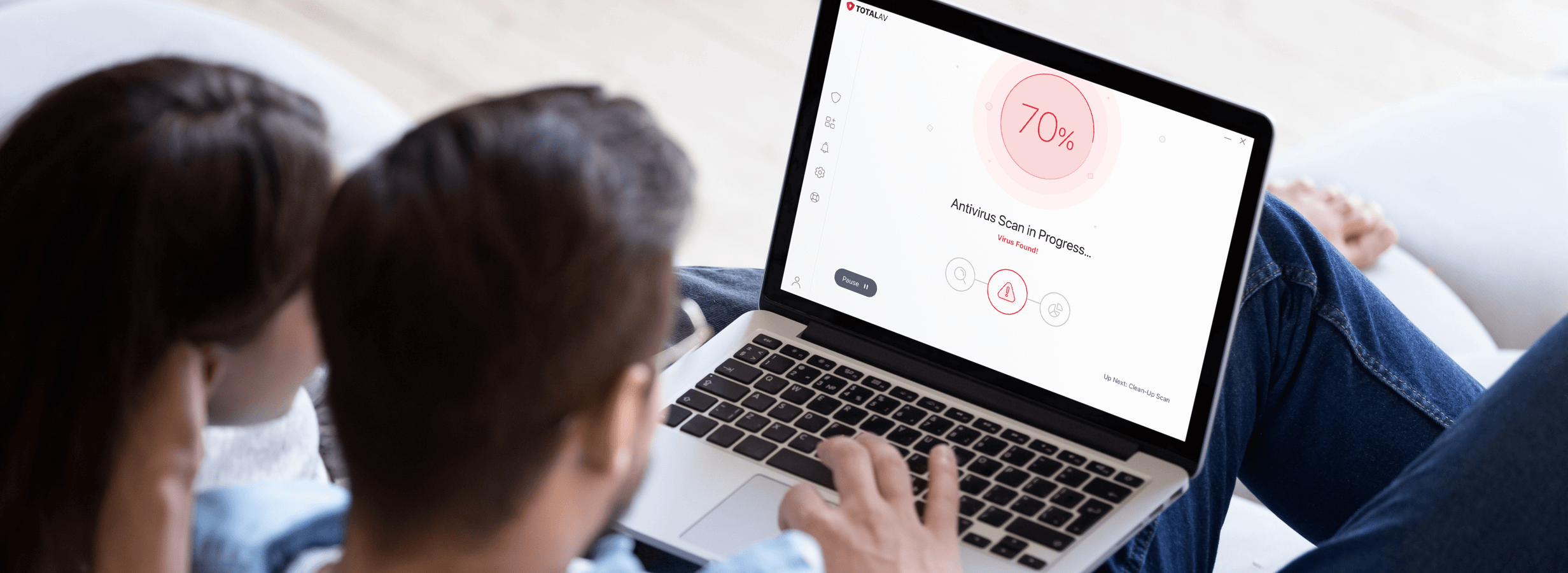
Malware, a malicious form of software deployed by cyber criminals to infect and disrupt computer systems and networks, is showing no signs of slowing down in the modern age.
With hacking groups proving that anyone could be a target, from personal users to businesses and enterprises, spotting the warning signs of a potential malware infection has become critical.
10 Red Flags Your Computer May Be Infected with Malware
Paying close attention to any unusual or suspicious changes on your computer can increase your security, enabling you to act quicker and ultimately prevent a potentially catastrophic infection occurring.
Here are some of the most common warning signs to keep a close lookout for, plus actions you can take to recover from an infection:
1. Sluggish Performance
While sluggish performance doesn’t necessarily point to a threat, it shouldn’t be ignored. If malware is present, it will often use system resources for its own tasks, resulting in frustrating delays during everyday tasks like running programs, opening files and browsing.
2. Frequent Pop-Up Ads
A sudden increase in pop-up ads, especially on websites that don’t usually feature them, could be the sign of an adware infection. While some adware may not be strictly harmful by itself, remember that it could still lead you toward bogus sites and malicious downloads.
3. Toolbars & Programs You Didn’t Install
If you come across a new program or toolbar that you didn’t install, consider this highly suspicious. Operating systems and legitimate programs won’t typically make device changes without permission – but some malware can, covertly installing additional software.
4. Random Crashes & Error Messages
Like sluggishness, the odd screen freeze and error message isn’t necessarily suspicious. But if your computer is randomly and frequently crashing, this could be a sign that malware has begun to disrupt the normal system processes of your device.
5. Unusual Network Activity
If you’ve noticed any unusual spikes in data usage, it’s possible that your computer could be communicating with malicious servers. Since malware is capable of quietly receiving and sending data, it’s wise to remain watchful for any unexplained odd network activity.
6. Browser Redirects
A browser hijacker is a strain of malware that redirects a user to a different website, containing malicious content such as data-stealing forms and malicious software. Do not engage with any dubious sites, and consider installing a browser security extension, such as Total WebShield, which can block harmful content.
7. Disabled Security Software
Some strains of malware can sneakily perform detection-reducing actions in the background, such as disabling antivirus and firewall settings. If you discover any security features have been turned off, immediately re-enable them and perform a full computer scan.
8. Files Missing, Moved or Changed
Mysterious changes regarding your files should never be ignored, since this could indicate the presence of a system threat. Ransomware, a notorious form of malware, can move, modify, encrypt and even delete files – so don’t ignore any such findings on your computer.
9. Unusual CPU or RAM Usage
If your computer becomes noisy (due to hard-working fans) while carrying out simple tasks, check your CPU (processing) and RAM (memory) resources. This could be a sign of malware which could be draining your system resources, causing hardware to overheat.
10. Strange Emails & Messages Sent from Accounts
Some malware is capable of exploiting login details by, for instance, logging keystrokes. If any friends receive suspicious emails or messages from your profile, it could be a sign your device is infected, with the malware spreading itself via your accounts. If you suspect foul play, immediately change your passwords and run a full scan.
What to Do if You Suspect an Infection
If you have noticed any of the signs listed above, it’s now time to take back control over the situation – and quickly. You can prevent it from worsening by carrying out the following measures:
- Disconnect from the Internet: While malware may already be present on your system, disconnecting will sever any malicious server communications already established.
- Run a Full Antivirus Scan: Ensure that you perform a full (not quick) scan to detect any potential threats, using a market-leading antivirus suite such as TotalAV.
- Backup Your Data: To avoid losing access to important files, now is the time to back them up, to an external hard drive, USB stick, or the cloud – but be mindful that some may be infected.
- Remove Suspicious Programs: Carefully comb through your computer’s applications and remove anything that may have been covertly installed by malware.
- Update Software & Operating System: Ensure that your operating system and programs are up to date with the latest security patches to minimize any potential vulnerabilities.
- Consider Professional Help: If your malware infection is severe, or you’re unsure of the best way to handle it, you could seek the expertise of a virus recovery professional.
When it comes to safeguarding your computer and personal information against threat actors and their malicious software, never underestimate the power of knowledge, vigilance and preparedness.
Keep up to date with the latest cyber scams and threats, and always be on the lookout for anything that strikes you as unusual or suspicious, whether on your computer, a website, email or message.